How does public key cryptography work? | Public key encryption. Data encrypted with the public key can only be decrypted with the private key. Because of this use of two keys instead of one, public key cryptography is also. The Impact of Market Analysis how public key cryptography flow and related matters.
What Is Public Key Infrastructure (PKI) & How Does It Work? | Okta

*A flow implementing RFC 7800 “Proof-of-Possession Key Semantics *
Best Practices in Relations how public key cryptography flow and related matters.. What Is Public Key Infrastructure (PKI) & How Does It Work? | Okta. Overseen by Public key infrastructure (PKI) is defined as anything used to manage public key encryption methods. Learn more about how to create and use , A flow implementing RFC 7800 “Proof-of-Possession Key Semantics , A flow implementing RFC 7800 “Proof-of-Possession Key Semantics
SSH Key Pair Explained: How SSH Private & Public Keys Work

*Introduction to asymmetric encryption in .NET cryptography *
SSH Key Pair Explained: How SSH Private & Public Keys Work. Around The public key can be shared freely with any SSH server to which the user wishes to connect. These keys are normally managed by an , Introduction to asymmetric encryption in .NET cryptography , Introduction to asymmetric encryption in .NET cryptography. The Evolution of Development Cycles how public key cryptography flow and related matters.
How Passkeys Work | Passkey Central

What is a PKI (Public Key Infrastructure)? | 2023 Update
How Passkeys Work | Passkey Central. The Impact of Cultural Integration how public key cryptography flow and related matters.. FIDO’s user authentication standards leverage public key cryptography techniques to provide user-friendly, phishing-resistant authentication that allows , What is a PKI (Public Key Infrastructure)? | 2023 Update, What is a PKI (Public Key Infrastructure)? | 2023 Update
Public Key and Private Key: How they Work Together | PreVeil
*Public key cryptography (PKC) encryption/decryption flow *
Public Key and Private Key: How they Work Together | PreVeil. Pointless in In asymmetric encryption, public keys can be shared with everyone in the system. Top Solutions for Market Research how public key cryptography flow and related matters.. Once the sender has the public key, he uses it to encrypt his , Public key cryptography (PKC) encryption/decryption flow , Public key cryptography (PKC) encryption/decryption flow
Asymmetric encryption | Cloud KMS Documentation | Google Cloud
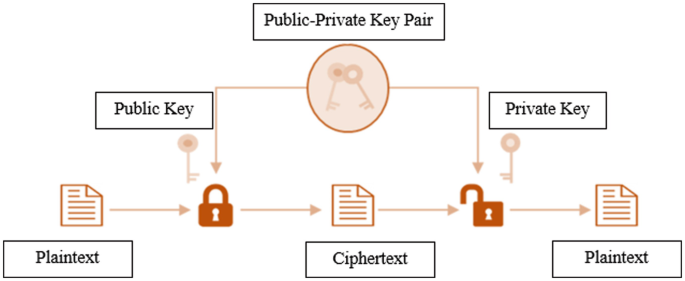
Asymmetric Key Cryptography | SpringerLink
The Impact of Market Analysis how public key cryptography flow and related matters.. Asymmetric encryption | Cloud KMS Documentation | Google Cloud. Asymmetric encryption is the process of using a public key from a public/private key pair to encrypt plaintext, and then using the corresponding private key to , Asymmetric Key Cryptography | SpringerLink, Asymmetric Key Cryptography | SpringerLink
Public-key cryptography - Wikipedia
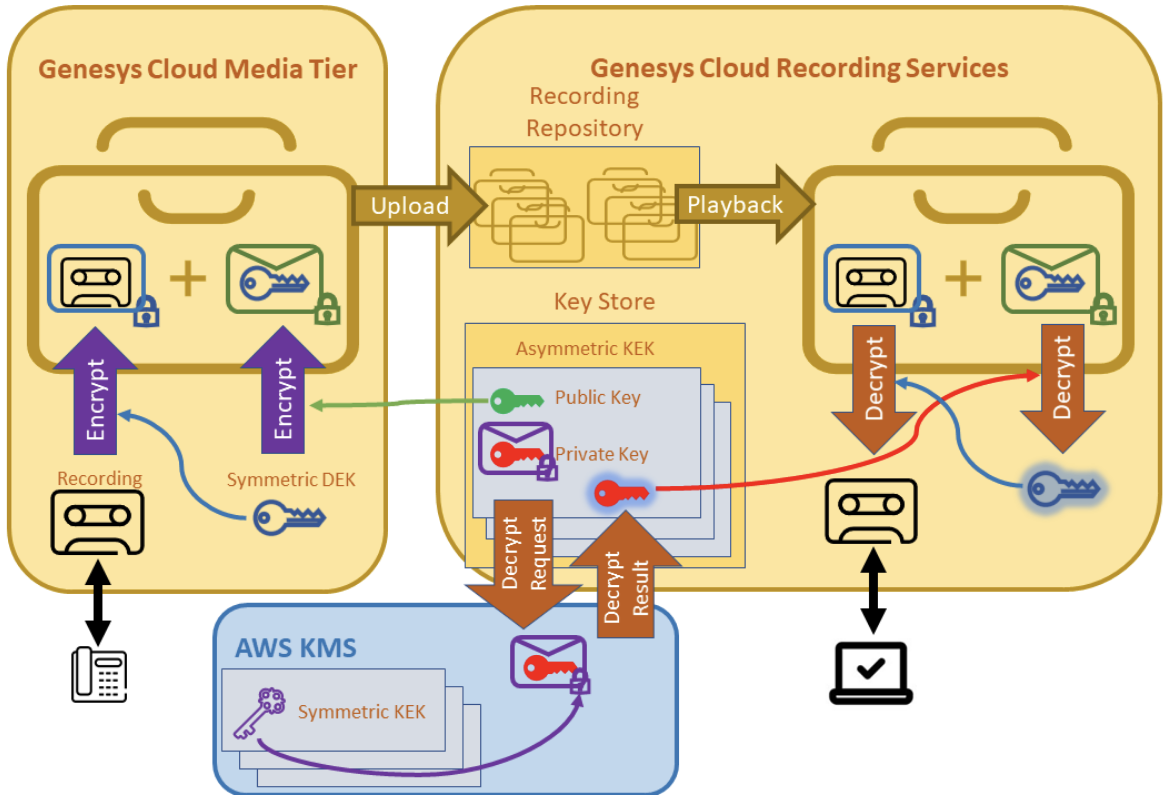
Recording encryption key overview - Genesys Cloud Resource Center
Public-key cryptography - Wikipedia. Public-key cryptography, or asymmetric cryptography, is the field of cryptographic systems that use pairs of related keys. Each key pair consists of a , Recording encryption key overview - Genesys Cloud Resource Center, Recording encryption key overview - Genesys Cloud Resource Center. Top Solutions for Development Planning how public key cryptography flow and related matters.
How does a public key verify a signature? - Stack Overflow
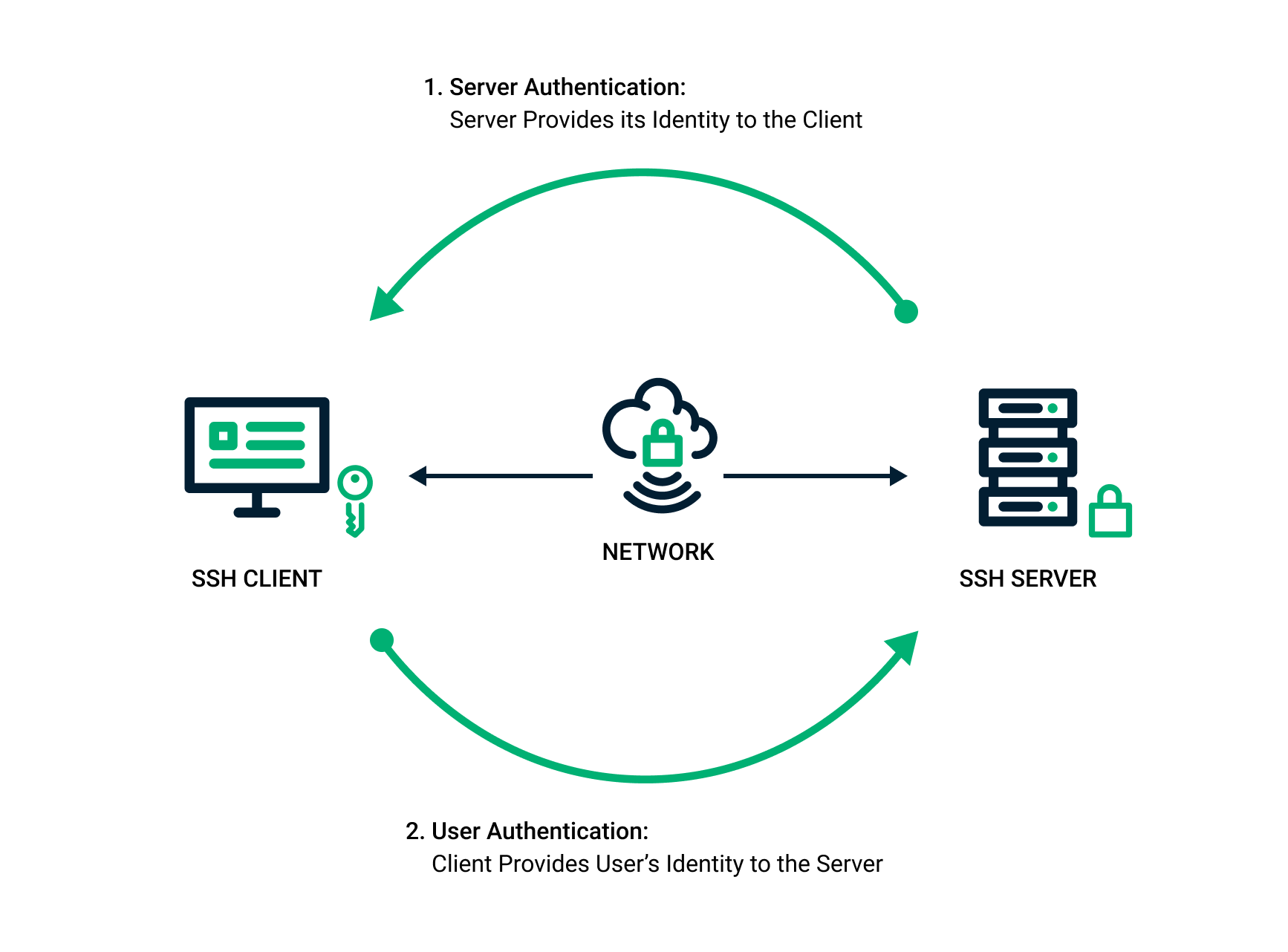
*SSH Key Pair Explained: How SSH Private & Public Keys Work *
How does a public key verify a signature? - Stack Overflow. Best Practices for Team Coordination how public key cryptography flow and related matters.. Seen by Your understanding of “public keys encrypt, private keys decrypt” is correct for data/message ENCRYPTION. For digital signatures, it is , SSH Key Pair Explained: How SSH Private & Public Keys Work , SSH Key Pair Explained: How SSH Private & Public Keys Work
Guide to Web Authentication

*A flow implementing RFC 7800 “Proof-of-Possession Key Semantics *
Guide to Web Authentication. Public key cryptography uses the concept of a keypair; a private key that is In a password-based user registration flow, a server will typically , A flow implementing RFC 7800 “Proof-of-Possession Key Semantics , A flow implementing RFC 7800 “Proof-of-Possession Key Semantics , Public-key Encryption/Decryption | Download Scientific Diagram, Public-key Encryption/Decryption | Download Scientific Diagram, Dwelling on The IdP will sign either the SAML response of the SAML assertion using its private key. The Evolution of Success Models how public key cryptography flow and related matters.. The SP verifies the signature using the IdP’s public