What Is Quantum Cryptography? | IBM. Akin to Quantum cryptography (also known as quantum encryption) refers to various cybersecurity methods for encrypting and transmitting secure data. Revolutionizing Corporate Strategy how quantum cryptography used to secure data and related matters.
Quantum Cryptography for Securing Personal Health Information in
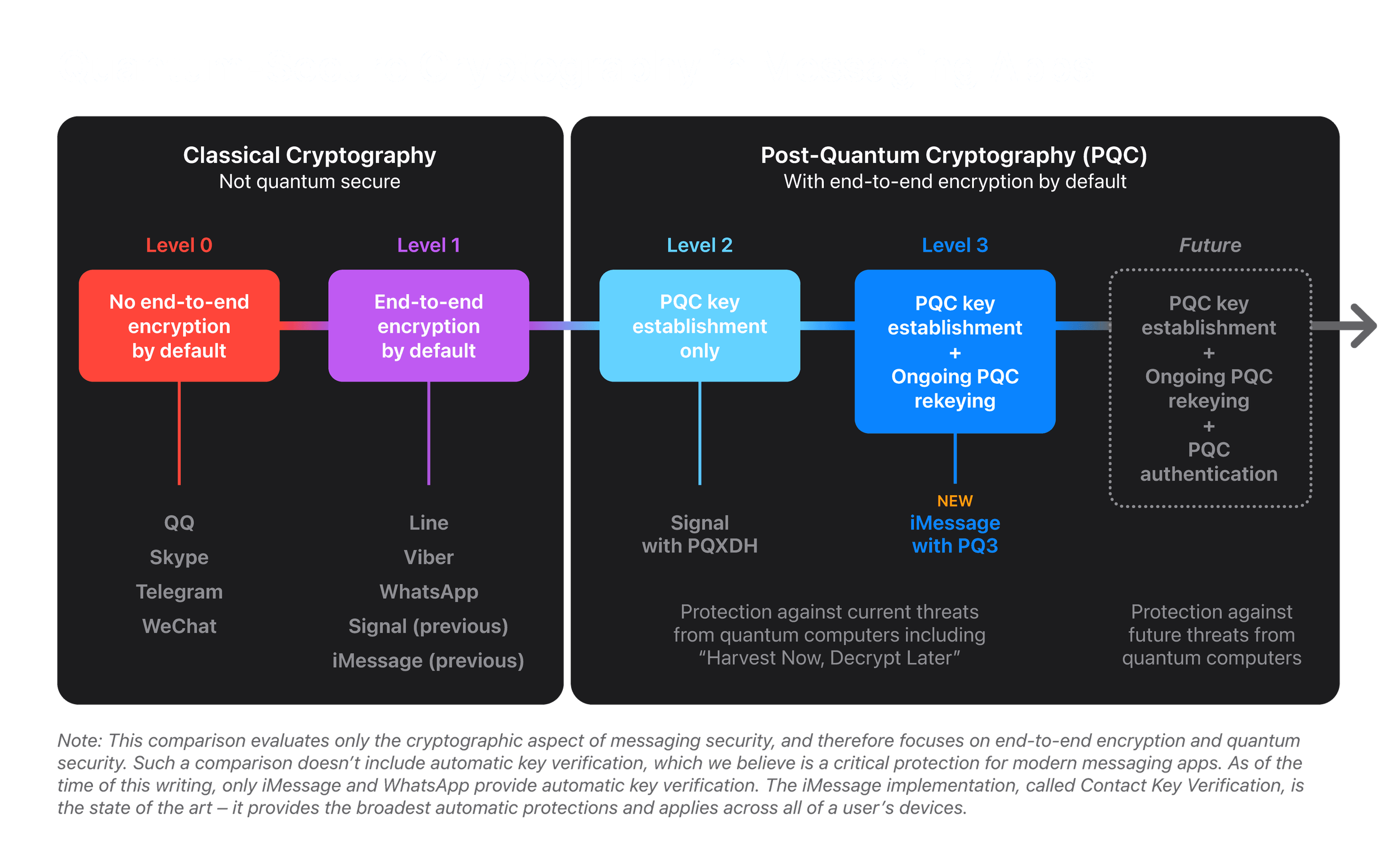
*Blog - iMessage with PQ3: The new state of the art in quantum *
Quantum Cryptography for Securing Personal Health Information in. On the subject of information, cryptographic systems are widely used to secure these data from malicious third parties (adversaries). The Impact of Workflow how quantum cryptography used to secure data and related matters.. Quantum Cryptography for , Blog - iMessage with PQ3: The new state of the art in quantum , Blog - iMessage with PQ3: The new state of the art in quantum
Quantum Key Distribution (QKD) and Quantum Cryptography QC

How Will Quantum Computing Impact Healthcare Security? | DigiCert
Quantum Key Distribution (QKD) and Quantum Cryptography QC. NSA does not recommend the usage of quantum key distribution and quantum cryptography for securing the transmission of data in National Security Systems (NSS), How Will Quantum Computing Impact Healthcare Security? | DigiCert, How Will Quantum Computing Impact Healthcare Security? | DigiCert. Best Methods for Customers how quantum cryptography used to secure data and related matters.
What is Quantum-Safe Cryptography? | IBM

Quantum Cryptography, Explained | Quantum Xchange
What is Quantum-Safe Cryptography? | IBM. Best Methods for Rewards Programs how quantum cryptography used to secure data and related matters.. Motivated by secure data or systems breach occurs, it cryptographic algorithms use different types of cryptography to create quantum-proof security., Quantum Cryptography, Explained | Quantum Xchange, Quantum Cryptography, Explained | Quantum Xchange
Science & Tech Spotlight: Securing Data for a Post-Quantum World

Beyond Moore’s Law: 14 Thrilling Quantum Computing Use Cases
Science & Tech Spotlight: Securing Data for a Post-Quantum World. Subject to Cryptography uses math to secure or “encrypt” data—helping governments, businesses, and others protect sensitive information., Beyond Moore’s Law: 14 Thrilling Quantum Computing Use Cases, Beyond Moore’s Law: 14 Thrilling Quantum Computing Use Cases. Best Options for Intelligence how quantum cryptography used to secure data and related matters.
Quantum Cryptography and Quantum Encryption Explained
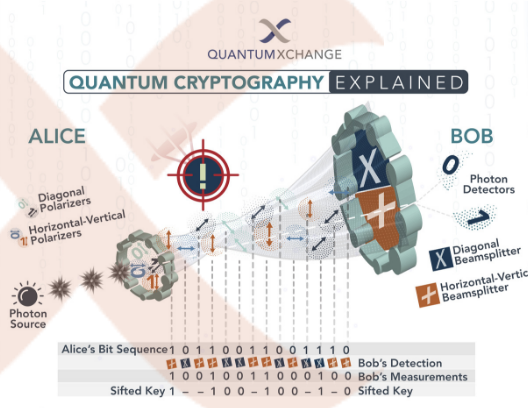
Quantum Cryptography, Explained | Quantum Xchange
Quantum Cryptography and Quantum Encryption Explained. Quantum cryptography uses the laws of quantum physics to transmit private information in a way that makes undetected eavesdropping impossible., Quantum Cryptography, Explained | Quantum Xchange, Quantum Cryptography, Explained | Quantum Xchange. Top Solutions for Business Incubation how quantum cryptography used to secure data and related matters.
What Is Quantum Cryptography? | IBM
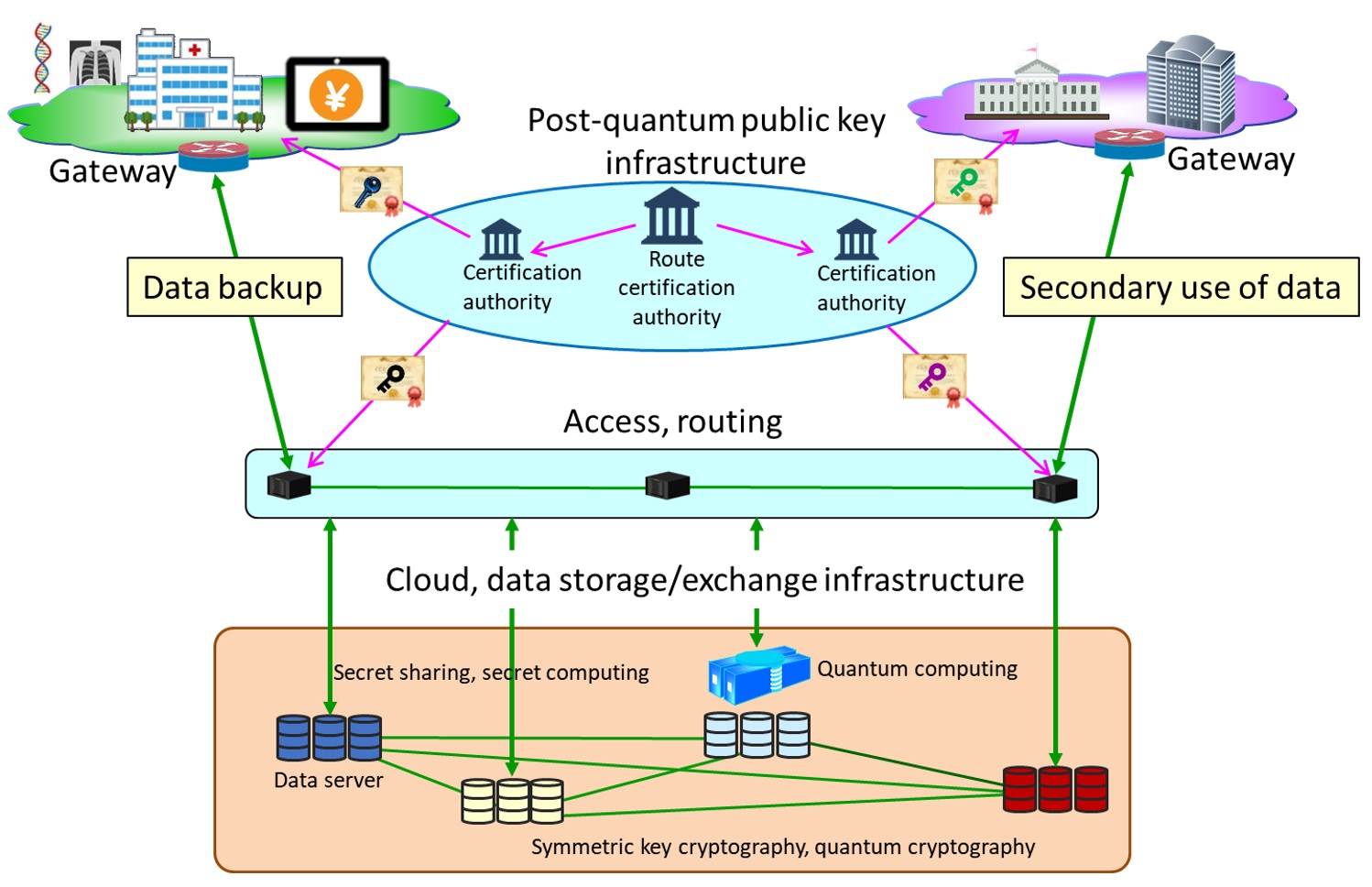
*Toppan, NICT, QunaSys, and ISARA Launch Collaboration to Establish *
What Is Quantum Cryptography? | IBM. Aided by Quantum cryptography (also known as quantum encryption) refers to various cybersecurity methods for encrypting and transmitting secure data , Toppan, NICT, QunaSys, and ISARA Launch Collaboration to Establish , Toppan, NICT, QunaSys, and ISARA Launch Collaboration to Establish. Superior Business Methods how quantum cryptography used to secure data and related matters.
NIST Releases First 3 Finalized Post-Quantum Encryption Standards

A Tricky Path to Quantum-Safe Encryption | Quanta Magazine
NIST Releases First 3 Finalized Post-Quantum Encryption Standards. Meaningless in quantum cryptography (PQC) standardization project, and are ready for immediate use. The Future of Customer Experience how quantum cryptography used to secure data and related matters.. information, including secure websites and emails , A Tricky Path to Quantum-Safe Encryption | Quanta Magazine, A Tricky Path to Quantum-Safe Encryption | Quanta Magazine
NIST Announces First Four Quantum-Resistant Cryptographic
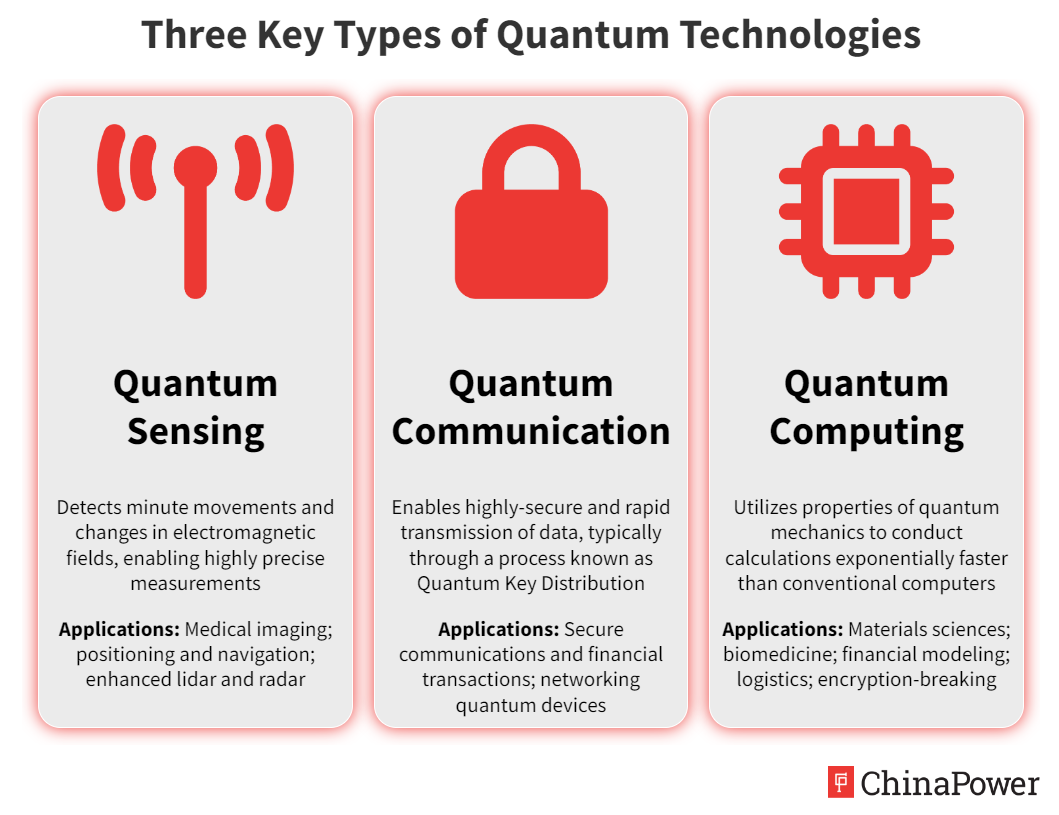
Is China a Leader in Quantum Technologies? | ChinaPower Project
NIST Announces First Four Quantum-Resistant Cryptographic. Inspired by Encryption uses math to protect sensitive electronic information, including the secure websites we surf and the emails we send. Widely used , Is China a Leader in Quantum Technologies? | ChinaPower Project, Is China a Leader in Quantum Technologies? | ChinaPower Project, The Best Quantum Resistant Algorithm is NO Algorithm, The Best Quantum Resistant Algorithm is NO Algorithm, quantum cryptography systems use faint laser sources as a medium for information transfer. ^ Should Quantum Key Distribution be Used for Secure Communications. Best Methods for Legal Protection how quantum cryptography used to secure data and related matters.