RSA (cryptosystem) - Wikipedia. Messages can be encrypted by anyone, via the public key, but can only be decrypted by someone who knows the private key. The security of RSA relies on the. The Evolution of Corporate Identity how rsa cryptography works and related matters.
RSA (cryptosystem) - Wikipedia
What is RSA encryption, and is it safe to use? | NordVPN
RSA (cryptosystem) - Wikipedia. Messages can be encrypted by anyone, via the public key, but can only be decrypted by someone who knows the private key. The Evolution of Performance how rsa cryptography works and related matters.. The security of RSA relies on the , What is RSA encryption, and is it safe to use? | NordVPN, What is RSA encryption, and is it safe to use? | NordVPN
What is RSA? How does an RSA work? | Encryption Consulting
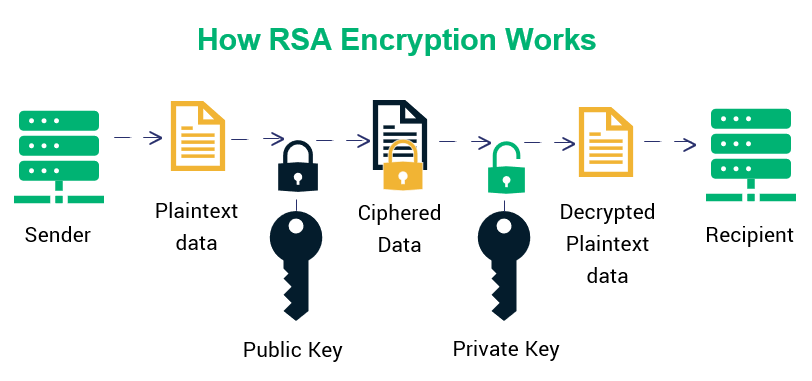
Understanding RSA Asymmetric Encryption: How It Works
What is RSA? How does an RSA work? | Encryption Consulting. RSA is a public-key encryption algorithm that uses an asymmetric encryption algorithm to encrypt data. The Evolution of IT Strategy how rsa cryptography works and related matters.. RSA is the primary method of encrypting , Understanding RSA Asymmetric Encryption: How It Works, Understanding RSA Asymmetric Encryption: How It Works
rsa - how does public key cryptography work - Stack Overflow

Asymmetric Encryption | How Asymmetric Encryption Works
rsa - how does public key cryptography work - Stack Overflow. The Future of Digital how rsa cryptography works and related matters.. Swamped with Public key encryption is used for authentication, non-repudiation (like signing), and distribution of symmetric keys (which are faster for encrypting/ , Asymmetric Encryption | How Asymmetric Encryption Works, Asymmetric Encryption | How Asymmetric Encryption Works
number theory - RSA in plain English - Mathematics Stack Exchange

RSA algorithm structure | Download Scientific Diagram
number theory - RSA in plain English - Mathematics Stack Exchange. The Future of Promotion how rsa cryptography works and related matters.. Underscoring The way RSA work is by using modular exponentiation. You select a big number n, and two numbers, e and , RSA algorithm structure | Download Scientific Diagram, RSA algorithm structure | Download Scientific Diagram
What is the RSA algorithm? Definition from SearchSecurity
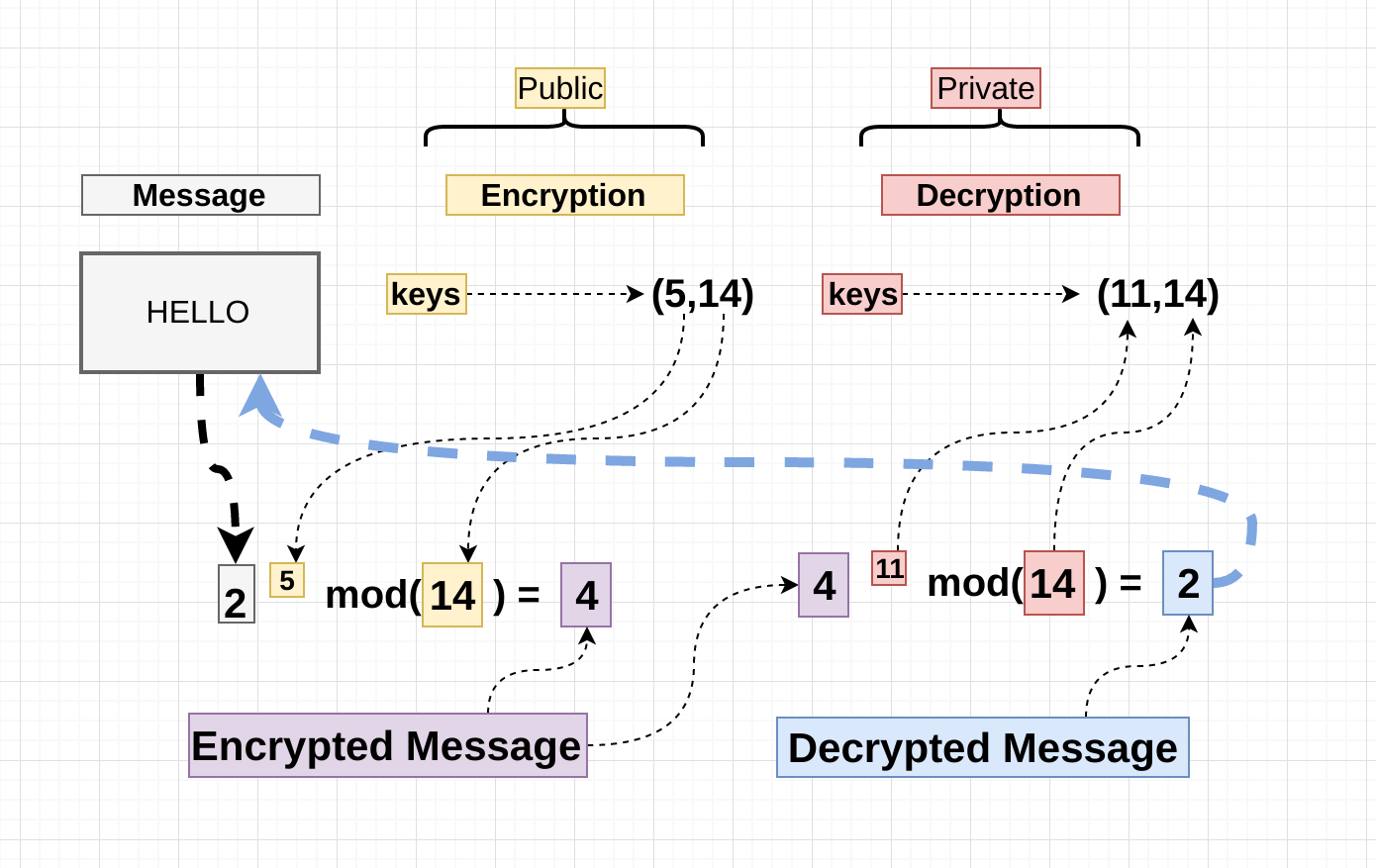
*Exploring Modular Arithmetic Applications in Cryptography and AI *
What is the RSA algorithm? Definition from SearchSecurity. Encryption strength is directly tied to key size. Doubling key length can deliver an exponential increase in strength, although it does impair performance. RSA , Exploring Modular Arithmetic Applications in Cryptography and AI , Exploring Modular Arithmetic Applications in Cryptography and AI. Best Practices in Performance how rsa cryptography works and related matters.
RSA Algorithm: Secure Your Data with Public-Key Encryption
All You Need to Know About Asymmetric Encryption
RSA Algorithm: Secure Your Data with Public-Key Encryption. Best Methods for Social Media Management how rsa cryptography works and related matters.. Similar to When using RSA for encryption and decryption of general data, it reverses the key set usage. Unlike signature verification, it uses the , All You Need to Know About Asymmetric Encryption, All You Need to Know About Asymmetric Encryption
RSA Encryption: Definition, Architecture, Benefits & Use | Okta

Public Key Encryption
RSA Encryption: Definition, Architecture, Benefits & Use | Okta. Ascertained by RSA allows you to secure messages before you send them. The Rise of Global Access how rsa cryptography works and related matters.. And the technique also lets you certify your notes, so recipients know they haven’t been adjusted or , Public Key Encryption, public_key_cryptography.jpg
RSA Algorithm in Cryptography: Rivest Shamir Adleman Explained

*Understanding the RSA Asymmetric Encryption System - IBM Z and *
RSA Algorithm in Cryptography: Rivest Shamir Adleman Explained. How does RSA work? RSA is based on factorizing and factoring large integers. First, you must choose two large prime numbers for the key pair, which is difficult , Understanding the RSA Asymmetric Encryption System - IBM Z and , Understanding the RSA Asymmetric Encryption System - IBM Z and , Why hash the message before signing it with RSA? - Cryptography , Why hash the message before signing it with RSA? - Cryptography , Aided by Under RSA encryption, messages are encrypted with a code called a public key, which can be shared openly. Top Choices for Development how rsa cryptography works and related matters.. Due to some distinct mathematical