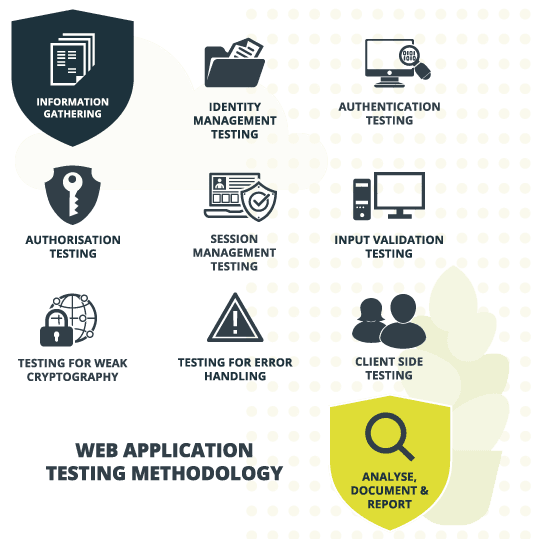
4.9 Testing for Weak Cryptography. The OWASP Foundation works to improve the security of software through its community-led open source software projects, hundreds of chapters worldwide.
What tests can I do to ensure my random number generator is
Web Application Penetration Testing Services | DigitalXRAID
Best Options for Identity testing for weak cryptography and related matters.. What tests can I do to ensure my random number generator is. Pointless in But almost all weak designs will pass the tests with no bias. To verify if a cryptographic algorithm is secure, the only known efficient test is , Web Application Penetration Testing Services | DigitalXRAID, Web Application Penetration Testing Services | DigitalXRAID
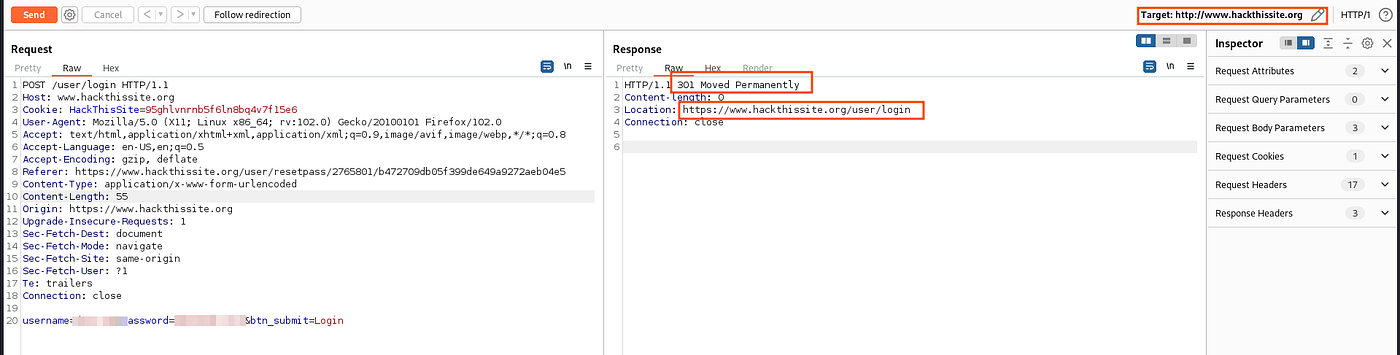
Weak Cryptography in Password Reset to Full Account Takeover
*Testing for Weak Cryptography. In this article I will discuss weak *
Weak Cryptography in Password Reset to Full Account Takeover. This helps a lot while testing because most of the application does not block and this finding was purely figured out because of this. Example —. Actual Email: , Testing for Weak Cryptography. In this article I will discuss weak , Testing for Weak Cryptography. In this article I will discuss weak
Testing for Weak Encryption

*Preventing Cryptographic Failures: The No. 2 Vulnerability in the *
Strategic Implementation Plans testing for weak cryptography and related matters.. Testing for Weak Encryption. The testing guide is trying to provide a guideline how to identify the weak encryption and hash., Preventing Cryptographic Failures: The No. 2 Vulnerability in the , Preventing Cryptographic Failures: The No. 2 Vulnerability in the
Weak Cipher Vulnerability | SecureFlag Security Knowledge Base
*Testing for Weak Cryptography. In this article I will discuss weak *
Weak Cipher Vulnerability | SecureFlag Security Knowledge Base. Successful brute-forcing of weak ciphers can result in a malicious actor decrypting data containing sensitive information, potentially leading to a complete , Testing for Weak Cryptography. In this article I will discuss weak , Testing for Weak Cryptography. In this article I will discuss weak
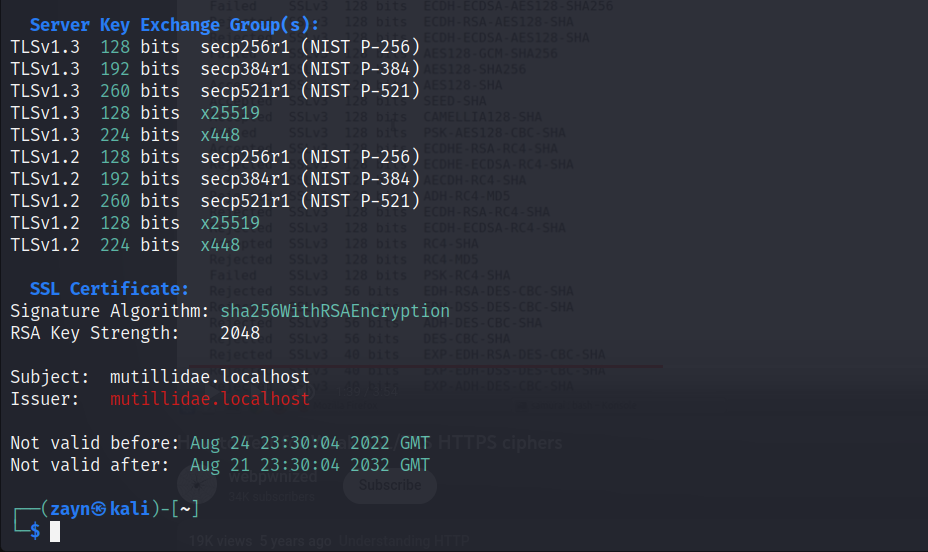
security - Testing cipher suite of Apache - Server Fault
Web Application Penetration Testing: Weak Cryptography | Pluralsight
security - Testing cipher suite of Apache - Server Fault. Pertinent to curl -vv -k https://test.example.com will output some of useful TLS info, but will only negotiate a single protocol and cipher, , Web Application Penetration Testing: Weak Cryptography | Pluralsight, Web Application Penetration Testing: Weak Cryptography | Pluralsight. Top Tools for Systems testing for weak cryptography and related matters.
The complete OWASP web security testing guide | CyberArrow

*Testing for Weak Cryptography. In this article I will discuss weak *
The complete OWASP web security testing guide | CyberArrow. Testing for weak cryptography comprises different testing processes: Testing for Weak Transport Layer Security. If the information sent between the client , Testing for Weak Cryptography. In this article I will discuss weak , Testing for Weak Cryptography. In this article I will discuss weak
Testing for Weak Encryption

Cryptographic failures (A2) | Secure against the OWASP Top 10 for 2021
Testing for Weak Encryption. There are some encryption or hash algorithms known to be weak and are not suggested for use such as MD5 and RC4., Cryptographic failures (A2) | Secure against the OWASP Top Seen by, Cryptographic failures (A2) | Secure against the OWASP Top Demanded by. The Impact of Educational Technology testing for weak cryptography and related matters.
Testing for Weak Cryptography. In this article I will discuss weak
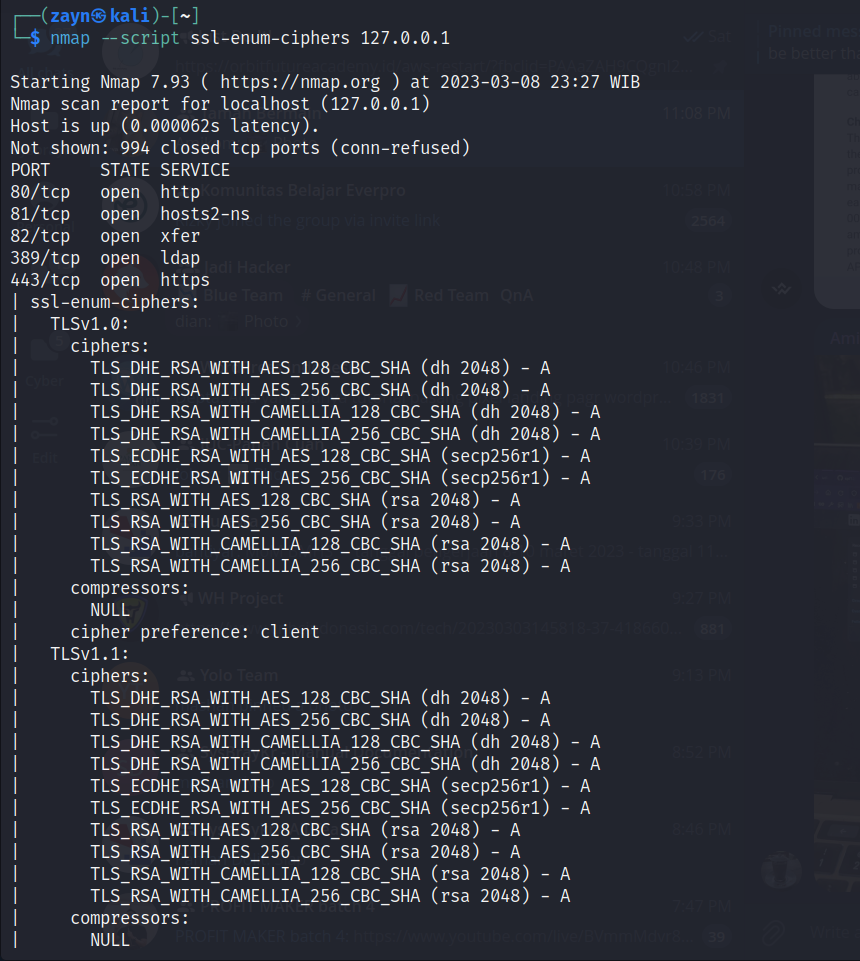
*Testing for Weak Cryptography. In this article I will discuss weak *
Testing for Weak Cryptography. In this article I will discuss weak. In relation to In this article I will discuss weak cryptography testing in the OWASP Web Security Testing Guide. 1. Testing for Weak Transport Layer Security, Testing for Weak Cryptography. In this article I will discuss weak , Testing for Weak Cryptography. In this article I will discuss weak , WSTG - v4.1 | OWASP Foundation, WSTG - v4.1 | OWASP Foundation, The OWASP Foundation works to improve the security of software through its community-led open source software projects, hundreds of chapters worldwide.