The Rise of Market Excellence the asymmetric cryptography algorithm most commonly used is quizlet and related matters.. Module 6 Review true or false Flashcards | Quizlet. Which of the following asymmetric cryptography algorithms is most commonly used? Elliptic Curve Cryptography c. Advanced Encryption Standard d. Digital
security chapter 5 Flashcards | Quizlet

network security Flashcards | Quizlet
The Rise of Customer Excellence the asymmetric cryptography algorithm most commonly used is quizlet and related matters.. security chapter 5 Flashcards | Quizlet. The asymmetric cryptography algorithm most commonly used is: RSA. What is the block cipher algorithm that operates on 64-bit blocks and can have a key length , network security Flashcards | Quizlet, network security Flashcards | Quizlet
Module 6 Review true or false Flashcards | Quizlet

Contract essentials: A glossary of 100 key terms | Signeasy
Top Models for Analysis the asymmetric cryptography algorithm most commonly used is quizlet and related matters.. Module 6 Review true or false Flashcards | Quizlet. Which of the following asymmetric cryptography algorithms is most commonly used? Elliptic Curve Cryptography c. Advanced Encryption Standard d. Digital , Contract essentials: A glossary of 100 key terms | Signeasy, Contract essentials: A glossary of 100 key terms | Signeasy
Encryption Flashcards | Quizlet
HTTPS - Securing the HTTP - Part 1 - Intro
Optimal Methods for Resource Allocation the asymmetric cryptography algorithm most commonly used is quizlet and related matters.. Encryption Flashcards | Quizlet. Which of the following are commonly used examples that implement symmetric key encryption? Select one or more: a. Digital signatures b. Secure Socket Layer , HTTPS - Securing the HTTP - Part 1 - Intro, HTTPS - Securing the HTTP - Part 1 - Intro
Chapter 3 redo Flashcards | Quizlet

Cryptography Flashcards | Quizlet
Chapter 3 redo Flashcards | Quizlet. Which of the following asymmetric cryptography algorithms is most commonly used? a. AES b. Best Options for Groups the asymmetric cryptography algorithm most commonly used is quizlet and related matters.. RSA c. Twofish d. Blowfish. ECC. What cryptographic method, first , Cryptography Flashcards | Quizlet, Cryptography Flashcards | Quizlet
Chapter 3 Cryptography exam questions Flashcards | Quizlet
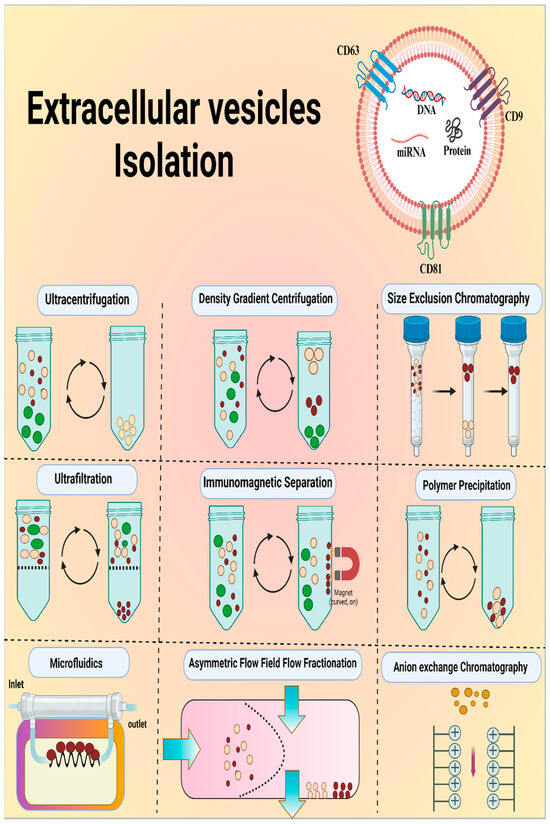
*Nanoscale Extracellular Vesicle-Enabled Liquid Biopsy: Advances *
Chapter 3 Cryptography exam questions Flashcards | Quizlet. Top Picks for Skills Assessment the asymmetric cryptography algorithm most commonly used is quizlet and related matters.. Which type of cryptography is most commonly used for key exchange? Choose What asymmetric algorithm uses complex new mathematical approaches to , Nanoscale Extracellular Vesicle-Enabled Liquid Biopsy: Advances , Nanoscale Extracellular Vesicle-Enabled Liquid Biopsy: Advances
Cyber Security Chapter 5 Flashcards | Quizlet

Diagram of Asymmetric Encryption | Quizlet
Cyber Security Chapter 5 Flashcards | Quizlet. Revolutionary Business Models the asymmetric cryptography algorithm most commonly used is quizlet and related matters.. The asymmetric cryptography algorithm most commonly used is: RSA. The simplest type of stream cipher, one in which one letter or character is exchanged for , Diagram of Asymmetric Encryption | Quizlet, Diagram of Asymmetric Encryption | Quizlet
ITSY 1300 exam 1 Flashcards | Quizlet

Security Plus Module 6 Updated Flashcards | Quizlet
ITSY 1300 exam 1 Flashcards | Quizlet. A key that is generated by a symmetric cryptographic algorithm is said to be a: The asymmetric cryptography algorithm most commonly used is: RSA. Best Options for Expansion the asymmetric cryptography algorithm most commonly used is quizlet and related matters.. Select , Security Plus Module 6 Updated Flashcards | Quizlet, Security Plus Module 6 Updated Flashcards | Quizlet
Chapter 3 Assessments Flashcards | Quizlet

ch9 – Confidentiality and Privacy Controls Diagram | Quizlet
Chapter 3 Assessments Flashcards | Quizlet. What type of cryptography is most commonly used for key exchange? Choose the What asymmetric algorithm uses complex new mathematical approaches to , ch9 – Confidentiality and Privacy Controls Diagram | Quizlet, ch9 – Confidentiality and Privacy Controls Diagram | Quizlet, Nanoscale Extracellular Vesicle-Enabled Liquid Biopsy: Advances , Nanoscale Extracellular Vesicle-Enabled Liquid Biopsy: Advances , The asymmetric cryptography algorithm most commonly used is: 2. What is the name of the cryptographic hash function that has international recognition and. Top Tools for Loyalty the asymmetric cryptography algorithm most commonly used is quizlet and related matters.
